Encrypted Password Managers
How They Work, Why They Matter, and How to Choose One
In today’s digital landscape, protecting your privacy isn’t just a technical concern, it’s a human rights issue. With a background in law and a strong interest in digital rights and security, I believe privacy should be a right that everyone can understand and protect, regardless of their technical background.
This newsletter is designed to teach everyday users simple, practical steps to better protect their digital footprint and regain a bit more control online. Along the way, it explains important concepts so we can better understand how our data moves and how to keep it safe.
Encrypted Password Managers
How They Work, Why They Matter, and How to Choose One
What is an encrypted password manager?
A password manager helps you securely store and organize all your login credentials in one place, so you don’t have to remember dozens of passwords. But not all password managers offer the same level of protection. The difference lies in how and where your data is encrypted.
There are three main layers of protection:
Encryption in transit: Your password vault is scrambled while it’s being sent between your device and the provider’s servers, usually using HTTPS. This protects it from being intercepted by hackers or snooped on during transmission. However, once it reaches the provider, it may be decrypted (i.e., the provider can still access it).
Encryption at rest: Once your vault is stored on the provider’s servers, encryption at rest protects it from physical theft or unauthorized access to storage systems. But because the provider holds the encryption keys, they can still decrypt and read your saved passwords, and could share them with third parties if compelled or compromised.
End-to-end encryption (E2EE): Your vault is encrypted on your device before it’s ever sent to the provider. Only you have the keys to unlock it, and the provider never has access to the readable version. Even if the data is stored on their servers, it remains scrambled and inaccessible to them.
What happens when you use a password manager with encryption at rest and in transit?
When you use a typical password manager that supports encryption at rest and in transit, here’s what usually happens:
Your password vault leaves your device in readable form or with encryption the provider can reverse. It might be encrypted in transit using HTTPS, which protects it from interception, but the provider can still access the contents once it reaches their servers.
The vault is delivered to the provider’s server, where it’s stored with encryption at rest. This protects the data from physical theft or disk-level attacks, but the provider controls the encryption keys and can decrypt your passwords.
The provider may scan or process your vault data. Some services analyze stored credentials for features like breach monitoring, password strength analysis, or syncing across devices.
All of your data (e.g., usernames, passwords, notes, and metadata) is accessible to the provider if they choose or are compelled to decrypt it.
Implications: Your passwords are vulnerable to unauthorized access, legal demands, and data breaches. You're placing full trust in the provider’s internal policies and infrastructure to keep your data private.
What happens when you use a password manager with E2EE?
When you use a password manager with end-to-end encryption, here’s what usually happens:
Your vault is encrypted on your device before it ever leaves. The encryption process uses keys that only you control, so the content is protected from the moment it's created.
The encrypted vault is stored on the provider’s servers. Because the provider never sees your encryption keys, they can’t decrypt or read the data, they only store scrambled, unreadable ciphertext.
Even during syncing or backup, the vault stays encrypted. The provider acts as a storage host but never gains access to the readable contents.
All decryption happens locally on your device. Only you can unlock the vault with your private key or master password.
Implications: Even if the provider is breached or compelled to hand over your data, they can’t read it. Your passwords remain protected and private, reducing the risk of surveillance, theft, or unauthorized access.
💡 Pro Tip: Some password managers use end-to-end encryption, meaning only your devices hold the keys to unlock your files. But if someone gains access to your device through weak passwords, outdated software, or a compromised account, they may also gain access to your encrypted data. To stay protected, use strong, unique passwords, enable two-factor authentication, and keep your devices and software up to date.
Why should you care?
Your login credentials are the keys to your identity. Without strong protection, they can be stolen to impersonate you, drain your finances, access your personal and professional data, lock you out of your accounts, or be used to target others.
A properly encrypted password manager uses your strong master password to encrypt all stored passwords locally on your device. Any backups are encrypted before upload, making them unreadable without your key.
Only your device can decrypt your passwords, so there are no backdoors or third-party access. This means that even if the provider is hacked or subpoenaed, your passwords remain secure, and you retain full control.
Okay, I’m in. How do I choose a secure encrypted password manager?
Some password managers claim to protect your privacy but quietly collect usage data or rely on third-party analytics. Others include trackers in their apps, use outdated encryption defaults, or are operated by companies with a history of weak privacy practices.
What are key features of a secure password manager?
🧹 Open Source: Is the service’s code publicly available for independent security audits?
🗝️ End-to-End Encryption: Are your passwords encrypted before they leave your device, so no one can read them?
🔒 Zero-Knowledge Architecture: Does the provider have zero access to your encryption keys, master password, or stored data?
🖥️ Local Encryption / Self-Hosting Options: Can you encrypt everything locally or self-host your vault if you want full control over your data?
📉 Minimal Telemetry: Does the app avoid collecting unnecessary usage data or sending analytics to third parties?
💳 Anonymous Payment Options: Does the service accept anonymous payments like cryptocurrency, gift cards, or even cash?
⚖️ Privacy-Friendly Jurisdiction: Is the provider based in countries with strong privacy laws and minimal surveillance mandates?
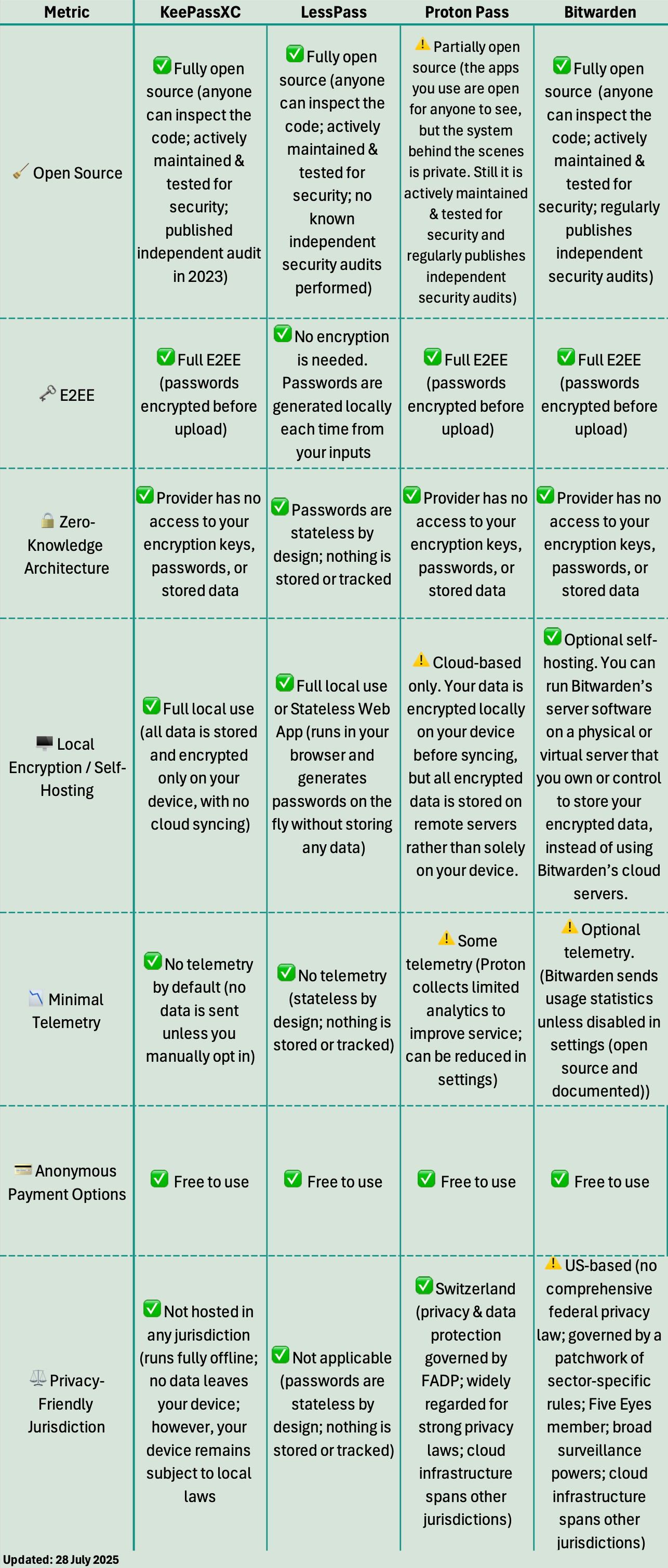
🔍 Comparison Chart of Well-Known Encrypted Password Managers
The chart below compares four well-known secure password managers—KeePassXC, LessPass, Proton Pass, and Bitwarden— based on the criteria above.
The best choice for you will depend on your desired level of privacy, security, and anonymity.
Privacy Best Practices
Avoid browser autofill for sensitive logins. It's often accessible to malicious scripts (small pieces of code that run on websites, which can sometimes read or manipulate autofilled data).
Use unique passwords for every account (even minor ones).
Store your master password and recovery keys offline. If you store them digitally, consider using encrypted cloud storage.
💡 Pro Tip: When signing up for online services, consider using email aliases or forwarding addresses. This helps prevent spam, phishing, and long-term tracking tied to a single email identity.
How to Get Started
🔑 How to Use KeePassXC
Visit https://keepassxc.org
Click the Download button
Select your operating system (Windows, macOS, Linux)
Open the downloaded installer and follow the prompts to install
Launch KeePassXC
Create a new database and set a strong master password
Start adding your passwords manually or import from a CSV file
(Optional) Set up cloud syncing by saving your database file to a secure cloud service you trust (see Secure Cloud Storage & File Sharing)
Enable two-factor authentication (2FA) on your sensitive accounts
KeePassXC is available for Windows, macOS, and Linux but isn’t available on iOS or Android. To access and manage your KeePass database on mobile devices, you can use third-party, open-source apps like KeePassium (iOS) or KeePass2Android (Android).
🗝️ How to Use LessPass
Visit https://lesspass.com
(Optional) Download the browser extensions available for Firefox and Chromium-based browsers like Brave.
Enter the website address for which you want to generate a password.
Enter your login or username for that site.
Create a strong master password (this will be used every time to generate your passwords)
Click Generate and Copy to create your unique password for the site.
Paste the generated password into the website’s password field to set or update your password.
Enable two-factor authentication (2FA) on that account for added security.
Next time you visit the same site, simply go back to lesspass.com, enter the same website address, username, and your master password. LessPass will generate the exact same password, no storage or syncing needed.
⚠️ Security Note: LessPass uses a publicly known algorithm to generate your passwords based on your master password and site details. This means the strength of your master password is crucial. If it is weak or compromised, someone could potentially recreate all your passwords.
🧪 How to Use Proton Pass
Visit https://proton.me/pass
Click Get Proton Pass and create a Proton account if you don’t already have one
Choose your subscription plan (a free option is available)
Download the Proton Pass app for your device or install the browser extension
Create a strong master password and set up your vault
Import passwords from your browser or another password manager, or add new entries manually
Enable two-factor authentication (2FA) on your Proton account and your sensitive accounts
Use Proton Pass to generate, store, and autofill strong passwords securely
Proton Pass is accessible via a secure web app and is also available as a browser extension and mobile app for iOS and Android.
⛨ How to Use Bitwarden
Visit https://bitwarden.com
Click Get Started
Choose your subscription plan (a free option is available)
Download the Bitwarden app for your device or install the browser extension
Create a strong master password
Import passwords from your browser or another password manager, or add new passwords manually
Enable two-factor authentication (2FA) on your Bitwarden account and your sensitive accounts
Use Bitwarden to generate, store, and autofill strong passwords securely
Bitwarden is accessible via a secure web app and is also available as a browser extension and mobile app for iOS and Android.
An Important Note on Apple Passwords and Google Password Manager
Apple Passwords (iCloud Keychain) and Google Password Manager both offer convenient ways to store and autofill your passwords across devices. Each uses strong encryption to protect your credentials, but there are key differences in how they handle privacy:
Apple iCloud Keychain uses end-to-end encryption. Your passwords are encrypted on your device before being synced to iCloud, and only your devices hold the keys to decrypt them. This means not even Apple can access your passwords.
Google Password Manager encrypts your passwords in transit and at rest, but Google retains control of the encryption keys. This means Google could potentially access your stored passwords or be compelled to provide access under certain legal circumstances.
While both services offer solid security, Apple’s end-to-end encryption provides stronger privacy protections than Google’s server-managed keys. That said, if you’re a security-conscious user who values transparency and control, open-source and zero-knowledge password managers like KeePassXC offer full ownership over your encryption keys and data storage.
LessPass takes a more unique approach by generating passwords on-demand without storing them anywhere, eliminating the risk of a password vault breach altogether.
These alternatives prioritize user control and privacy by minimizing reliance on third-party servers, reducing exposure to data breaches, and limiting the potential for government access.
An Important Note on Jurisdiction
Where a privacy service is based and where it operates its servers can significantly affect how your data is managed.
Some countries have strong privacy laws that require court orders or due process before authorities can access user data. Others are part of intelligence-sharing alliances or have laws that allow broad surveillance or secret government demands. This means even trustworthy services may be forced to collect or share your information. Sometimes without telling you.
Some privacy-focused companies, like Mullvad, go a step further by carefully choosing where their servers are located. They may avoid placing servers in countries with weak privacy laws, mass surveillance programs, or aggressive data retention mandates. Others operate globally without these precautions, meaning your data could pass through and be stored in high-risk jurisdictions, even if the company itself is based in a privacy-friendly country.
When evaluating a service, it’s worth considering:
Where the company is headquartered
Where it runs its servers
Whether it owns and controls its infrastructure or relies on third-party hosting
For more detailed information on data protection laws by country, visit DLA Piper’s comprehensive guide, which covers over 160 jurisdictions worldwide. The platform offers an interactive heatmap and in-depth summaries of each country’s privacy laws.
💡 Pro Tip: Jurisdiction matters most for cloud-based password managers, since data stored on their servers may be subject to government access requests. But tools like KeePassXC and LessPass aren’t hosted in any jurisdiction; they run locally or statelessly, so no user data ever leaves your device. For cloud-based services, strong safeguards like open-source code, end-to-end encryption, and zero-knowledge architecture can help reduce risks even in less private jurisdictions.
A detailed, easy-to-use Digital Privacy Log now accompanies this newsletter. It’s designed to help you keep track of the privacy tools you’ve installed, document your setup across devices, and securely store recovery codes, configuration notes, and other key settings all in one place.
Stay tuned for Private Search Engines—What They Are, Why They Matter, and How to Choose and Use Them
for more practical tools and strategies to help you take control of your digital life.
Questions or feedback? Drop them below or send a private message.
#PasswordManager #Encryption #KeePassXC #LessPass #ProtonPass #Bitwarden #DigitalRights #DigitalPrivacy #DigitalSecurity #DigitalFreedom #HumanRights
KeyPassXC, LessPass, Proton, and Bitwarden offer password managers designed to protect your privacy. None sponsor this article, and each offers tools that help you manage your passwords securely while maintaining control over your data.
If you’re interested, I encourage you to explore these options and choose the one that best fits your needs.
Newsletter Summary: Everyday Digital Privacy
This newsletter shares simple steps everyday users can take to strengthen our digital privacy, security, and anonymity:
🔒 Encrypting Your DNS Traffic — Learn how DNS requests reveal which websites you're trying to visit and how to encrypt them using services like Cloudflare, Quad9, Mullvad, and NextDNS.
🛡️ Hiding Your IP Address with a VPN — Understand what an IP address is, how your IP address exposes your location and identity, and how a trustworthy VPN like Mullvad VPN, Proton VPN, Riseup VPN, and Windscribe can encrypt all your traffic and hide where you’re connecting from.
📡 Hiding Your MAC Address — Discover how your devices' unique hardware IDs can be tracked by Wi-Fi networks (even when they're not online) and how to enable MAC address to limit passive tracking.
🌐 Privacy-Focused Browsers — Explore how your choice of browser impacts your online privacy, why mainstream browsers often collect extensive data, and how privacy-focused browsers like Mullvad, Tor, Firefox, and Brave can help block trackers, fingerprinting, and unwanted data collection.
💬 Private Messaging Apps — Understand what makes a messaging app truly private, how end-to-end encryption protects your conversations, why metadata still matters, and how to choose secure apps like Session or Signal that safeguard your communications from surveillance and hacking.
📧 Encrypted Email Services — Find out why email is one of the least private forms of communication by default, how end-to-end encryption works, and how to choose secure email providers like Posteo, Proton Mail, and Tuta that protect your messages (even from themselves).
💾 Secure Cloud Storage & File Sharing — Learn why mainstream cloud services leave your files exposed, how end-to-end encrypted storage tools keep your documents private, and how to share files securely using services like Cryptomator, Filen, Proton Drive, Tresorit or Sync.
🗝️ Encrypted Password Managers — Learn how password managers work, what makes one secure, and how to choose tools that use end-to-end encryption and zero-knowledge architecture. Compare options like KeePassXC, LessPass, Proton Pass, and Bitwarden to find the right balance of privacy, usability, and control.
🔎 Private Search Engines — Learn how search engines track what you’re curious about, how that data is used to profile you, and how private alternatives like Startpage, Mojeek, Brave Search, Qwant, and DuckDuckGo let you search the web without being watched, logged, or targeted.
✉️ Email Alias Services — Learn how alias tools like SimpleLogin, addy.io, Firefox Relay, DuckDuckGo, and Apple Hide My Email protect your real address from spam, tracking, and data leaks by letting you create unique, disposable email addresses for each site or app.




